- Blog, Cyber Security
- Published on: 16.12.2025
- 7:08 min
Human Firewall: When Awareness Becomes the Best Defense
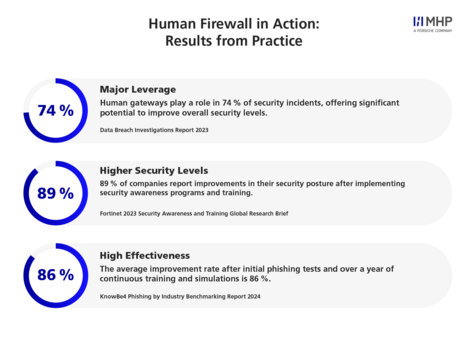
In 2024, global cybersecurity threats reached record highs. Every day, hundreds of thousands of new malware variants were detected worldwide. According to the 2024 Verizon Data Breach Investigations Report, 68% of data breaches are linked to human error caused by employees' unintentional actions, such as falling victim to phishing, social engineering, or using weak passwords. The message is clear: technology alone cannot prevent modern cyberattacks.
Global Cyber Threat Landscape at a Glance (2024):
Estimated global annual losses exceeding 10.5 trillion U.S. dollars due to cybercrime by 2025.
In 2023, malware attacks surged to 6.06 billion cases, with encrypted threats increasing by 117% and IoT malware rising by 107%. This demonstrates that cybercriminals are constantly evolving their methods.
Most successful breaches still involve the human element, proving the importance of a strong human firewall.
These figures highlight a simple truth: effective protection against cyberattacks requires more than just technology. It depends on people and building a well-informed, vigilant workforce. A strong human firewall transforms employees into the primary and most effective line of defense by fostering awareness, responsibility, and knowledge, thereby bolstering cybersecurity awareness throughout the entire organization.
Human Firewall: Definition and Strategic Importance
A human firewall is the organization-wide ability of employees to recognize cyber risks, respond appropriately, and apply security principles to their daily work. The goal of a strong human firewall is to turn employees into an active first line of defense that works seamlessly alongside technical solutions and organizational processes.
An effective human firewall depends on the strategic interaction between people, the organization, and technology. Although many successful cyberattacks are traced back to human error, this very factor can become the strongest line of defense through targeted communication, tailored training, and empowered employees.
Key characteristics of an effective human firewall include:
- Vigilance: Natural skepticism toward unusual requests and emails; attention to unauthorized individuals in the office; missing visitor badges; exposed confidential documents; and unsecured workstations.
- Informed: A solid understanding of current threats and security policies.
- Willingness to learn: Openness to continuous education and seeking guidance when uncertain.
- Responsibility: Awareness of one’s role in protecting the organization and prompt reporting of suspicious activities.
- Attention to detail: The ability to notice even the smallest digital (e.g., spelling errors or unusual sender addresses) and physical (e.g., improperly disposed documents, unlocked screens, or poorly stored confidential information) irregularities.
By fostering these qualities, organizations can strengthen their cybersecurity by turning employees into proactive defenders and reducing risks from everyday human errors.
Why Cybersecurity Needs Innovative Approaches
Modern cyberattacks are becoming increasingly complex and sophisticated. Attackers now exploit technical vulnerabilities and psychological manipulation techniques more systematically than ever, targeting the human factor.
For example, phishing attacks involve fake emails that falsely appear to come from trusted colleagues and can also operate without any malicious links or attachments. Through natural communication, these attacks target employees directly to initiate financial transactions, extract sensitive data, or carry out other harmful actions. These attacks become even more convincing when combined with AI tools: messages are well-written and free of spelling mistakes, they adapt automatically to the writing style of the impersonated person, and they can be sent in large volumes.
Artificial Intelligence also increases risk in other ways. AI-generated deepfake videos can simulate video conferences, and voice-cloning technologies can imitate a manager’s voice to make fraudulent phone calls.
Meanwhile, IT environments are becoming increasingly complex. New and legacy software are used side by side, entire work areas exist virtually, and systems are increasingly interconnected. These evolving workflows create opportunities for both employees and attackers.
Regulatory pressure adds another layer of complexity. The implementation of the NIS2 Directive in Germany, for example, significantly raises cybersecurity requirements and affects tens of thousands of companies. Organizations must also comply with standards such as ISO 27001 and TISAX, which require regular security training and proper handling of confidential information by all employees (ISO 27001 Control A.6.3). To meet these requirements, an effective human firewall is essential.
ISO 27001 and TISAX at a Glance:
ISO 27001 is an international standard for Information Security Management Systems (ISMS). It establishes systematic requirements for developing, implementing, and continuously improving information security within organizations, including employee awareness and training programs.
TISAX (Trusted Information Security Assessment Exchange) was originally developed by the automotive industry but is now relevant far beyond it. The assessment and exchange mechanism is comparable to ISO 27001 and therefore also defines requirements related to training and cybersecurity awareness. In addition, TISAX places particular emphasis on data protection, availability, and the protection of prototypes and other confidential information.
Therefore, building a strong human firewall is crucial. Well-trained, security-conscious employees are the first line of defense, helping organizations meet regulatory standards and strengthen protection against cyberattacks.
Beyond Training: The Modern Human Firewall
A future-ready human firewall goes far beyond traditional awareness training. It requires systematic integration into the ISMS as well as embedding within the organizational culture.
From awareness to cybersecurity culture
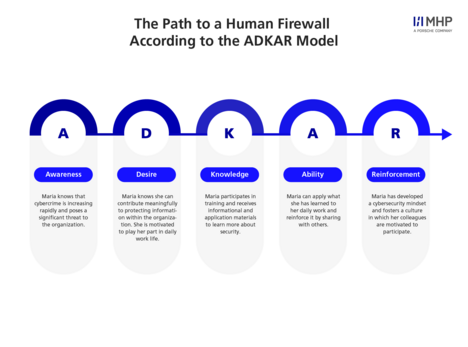
The path to a robust human firewall often follows this development trajectory: Awareness → Behavior → Culture. This transformation can be illustrated using the ADKAR® model from Prosci®. Implementing this model helps organizations build a strong human firewall cybersecurity posture.
- Awareness: Creating an understanding of cyber risks and their potential impact.
- Desire: Developing recognition of one’s role as part of the human firewall and the willingness to take responsibility for cybersecurity in daily work.
- Knowledge: Providing practical knowledge of threats and protective measures.
- Ability: Building the skills to detect and respond appropriately to threats.
- Reinforcement: Continuously reinforcing and embedding behavioral changes.
Structural enablers as success factors
The change process described by the ADKAR model requires appropriate organizational conditions to be successful. Only under these conditions can a sustainable cybersecurity culture emerge:
Organizational priority and resources: Adequate personnel, financial, and time resources must be allocated to cybersecurity initiatives. The number of employees dedicated to security, the available budget, and the time allotted for ongoing training are decisive factors in achieving success.
Leadership and role modeling: Leaders must actively support cybersecurity and integrate it as a natural part of their teams’ daily work. Management must practice what it preaches to earn real credibility.
Systematic integration: Cybersecurity must be embedded in all organizational processes, from onboarding new employees to strategic business development.
Strong structural support enables employees to effectively act as a human firewall, transforming cybersecurity awareness into tangible protection against cyberattacks throughout the organization.
Proven Measures and Formats for the Human Firewall
Achieving and continuously improving a strong level of maturity requires concrete measures. There are various targeted approaches to strengthening the human firewall, including those that cover awareness, communication, enablement, and training.
Awareness and communication:
- Cross-media slogan campaigns
- Newsletters with up-to-date threat alerts
- Interactive podcast formats
- Gamified quiz formats
- Regular Ask-Me-Anything sessions with IT security experts
- Targeted awareness programs on deepfake technologies
Enablement and training:
- Web-based learning platforms
- Hands-on, in-person training
- Compact how-to guides
- Continuous learning journeys
- Realistic phishing simulations
- Innovative formats, such as mobile escape trucks, make cybersecurity tangible
Key factors for sustainable success include:
- Frequency and cross-media integration: Regular security activities, such as phishing simulations, newsletters, and training, keep cybersecurity visible and prevent it from being deprioritized.
- Personalization: Training should be tailored to individual skill levels, languages, and roles.
- Gamification: Reward systems, point scoring, and other playful approaches can increase motivation and engagement.
- Positive reinforcement: Employees who correctly identify suspicious activity should be recognized rather than feared.
Human firewall examples like interactive simulations, gamified quizzes, and mobile escape trucks illustrate how organizations can turn employees into a proactive defense line. Implementing these measures strengthens cybersecurity awareness and enhances overall protection against cyberattacks.
How MHP Strengthens the Human Firewall and Cultivates a Culture of Cybersecurity
MHP views cyber resilience as the holistic interaction of people, organizations, and technology. Our human firewall approach combines strategic consulting with practical implementation measures.
We don't develop isolated awareness programs. Instead, we create systematic change processes that connect awareness, enablement, and culture.
- Awareness: Clear, understandable communication using storytelling and simple language
- Enablement: Gamified training, realistic simulations, and interactive learning formats tailored to specific target groups
- Culture: Continuous embedding of security culture across all roles and hierarchy levels through workshops and awareness or enablement sessions
Employees are guided individually on their journey to developing a cybersecurity mindset using the ADKAR change management approach. Tailored interventions consider personal motivations, habits, and learning preferences.
Key program components include:
- Development and execution of targeted awareness campaigns
- Creation of interactive training programs
- Professional community management to encourage experience sharing
- Practical quick guides for daily work
- Building a cybersecurity brand within the organization
This leads to measurable results for your organization:
- Increased security: Significantly fewer cyberattacks penetrate the human firewall.
- Lower costs: Reduced follow-up costs thanks to fewer incidents.
- Cultural shift: Cybersecurity becomes a lived value rather than a burdensome obligation.
- Compliance: Contributes to meeting regulatory requirements, such as NIS2, ISO 27001, and TISAX.
Empower your employees to become the most effective line of defense against cyberattacks. Together, we will develop a human firewall and embed cybersecurity sustainably into your organizational culture.
Conclusion: The Human Firewall as a Strategic Success Factor
Cybersecurity challenges are becoming increasingly complex with the advent of new technologies, most recently Artificial Intelligence. At the same time, humans remain central to most cyberattacks and must be systematically empowered to effectively defend against them. Three core principles are essential:
- All employees need individual support. The journey to a cybersecurity mindset is highly personal and requires holistic, tailored measures. Only then every employee can become an active part of the human firewall.
- Building a holistic cybersecurity culture is essential. A strong security culture arises from the interaction of people, structural enablers, and organizational conditions. Measurable security and sustainable cultural impact are achieved when technology, organization, and people work in harmony.
- The time to act is now. Regulatory requirements are increasing, attacks are becoming more sophisticated, and potential damages are reaching record levels. Companies that invest early in their human firewall achieve compliance and develop a lasting competitive advantage.
The human firewall is an ongoing process of empowerment and cultural development. By consistently following this path, you can transform the greatest security risk into the strongest line of defense. We are ready to support you every step of the way.
FAQs
A human firewall is a strategic security concept that transforms employees into an effective initial defense against cyberattacks. Since 68% of data breaches involve human error, it's clear that technical solutions alone aren't enough. A well-trained and aware workforce can recognize and stop attacks before they cause damage.
The human firewall complements technical protection with human attention, knowledge, and correct behavior. It transforms the potentially largest security vulnerability into an effective defense within the organization’s network.
A successful cybersecurity culture relies on three pillars. First, the systematic empowerment of employees through continuous training and realistic simulations. Second, structural enablers, such as sufficient resources, leadership support, and clear responsibilities. Third, measurable integration into all organizational processes, from hiring to strategic planning.
Leaders are critical to the success of a human firewall. They must actively model cybersecurity, provide adequate resources, and integrate security practices into their teams’ daily work. A culture where employees feel empowered to prioritize security will only emerge when management establishes and supports cybersecurity as a core value. Without credible leadership engagement, security initiatives remain ineffective and superficial.